Find Weaknesses Before They Find You.
Tech360 helps you identify, assess, and eliminate vulnerabilities before they turn into full-blown security incidents. Our experts uncover the cracks in your armor – and then make sure they stay sealed.


The Reality of Modern Vulnerabilities
In cybersecurity, the smallest gap can cause the biggest headache. All it takes is one unpatched system or outdated library to open the door for an intruder who never sleeps.
Vulnerabilities aren’t rare; they’re constant. Every piece of technology – every device, line of code, and user login – creates a potential security vulnerability. But panic isn’t the answer. Discipline is.
At Tech360, we treat vulnerability management like a living process, not a quarterly report. From identifying software vulnerabilities to mitigating network vulnerabilities, we bring order to digital chaos – keeping your systems hardened, compliant, and ready for what’s next.
Key Offerings
Here’s a peek at our full suite of services at your beck and call when it comes to vulnerability management and containment.
Vulnerability Assessment and Prioritization
Continuous Monitoring and Patch Management
Threat Intelligence and Risk Correlation
Network Vulnerability Analysis
Incident Readiness and Remediation
Why Vulnerability Management Matters
A breach rarely happens because of a genius hacker; it happens because of a missed patch, a lazy password, or a misconfigured firewall.
Most organizations don’t fail due to lack of investment; they fail due to lack of visibility. Vulnerability management bridges that gap.
We find, classify, and prioritize every cyber vulnerability in your ecosystem – helping you understand which weaknesses pose real risk, and which are just noise.
Because the truth is: you can’t fix what you don’t see, and you shouldn’t fear what you can control.
The Future of Vulnerability Management in 2026 and Beyond
If 2020 was about finding flaws, 2026 will be about predicting them. The landscape of vulnerability management is shifting from “reactive patching” to “proactive prevention.” The idea is no longer to fix problems after they arise -but to anticipate the next security vulnerability before it has a chance to breathe.
At Tech360, we’re already seeing signs of that future. It’s smarter, faster, and, oddly enough, more human than anyone expects.






Predictive Defense Will Replace Reactive Response
Machine learning and AI-driven analytics will make guessing obsolete. Organizations will use predictive algorithms to detect emerging software vulnerabilities in real time, before traditional scanners even know they exist.
These systems will analyze behavior patterns, code dependencies, and exploit trends, enabling companies to fix potential weaknesses before they’re found by an attacker.
Continuous Monitoring Becomes Continuous Assurance
The new era of cyber vulnerability management won’t stop at scanning; it’ll measure resilience. Security systems will automatically detect, classify, and remediate risks, providing what we’ll call “Assurance-as-a-Service.”
Tech360 envisions an ecosystem where vulnerabilities are identified, prioritized, and patched in a single loop -no waiting, no oversight fatigue, no human bottleneck.
Human Oversight Will Matter More Than Ever
Here’s the twist -automation can catch thousands of system vulnerabilities, but only people can judge which ones actually matter. The future will demand teams who can interpret machine findings in business context. That’s where Tech360’s hybrid approach -automation plus human expertise -becomes the gold standard for accuracy and prioritization.
Regulations Will Get Smarter (and Stricter)
By 2026, regulators will expect continuous vulnerability assessments, not just annual checkboxes. Enterprises will need to prove they’re managing network vulnerabilities in real time, with transparent reporting and immutable audit trails. Compliance will evolve from being a task to being an embedded behavior -and Tech360’s solutions are designed for that future.
Integration Across Ecosystems
The future of software vulnerability management lies in unification -integrating security tools, CI/CD pipelines, and cloud environments under one intelligent dashboard.
No more silos, no more blind spots -just synchronized, data-driven control that blends security with agility.
From Detection to Prevention
By the end of the decade, penetration testing won’t just identify vulnerabilities; it will predict them. Using predictive analytics and real-time telemetry, future systems will flag potential exploit chains before they exist.
The future won’t just be about defending; it’ll be about outsmarting.
The takeaway
Tomorrow’s vulnerability management won’t be about reacting faster; it’ll be about not needing to react at all. At Tech360, we’re helping businesses build that reality today -where prevention is instinct, not reaction, and visibility is a constant, not a luxury.
Challenges Security Vulnerability Management Will Face in 2026 and Beyond
Of course, the future never arrives quietly. For every advancement in cyber vulnerability detection, there’s an equal and opposite headache waiting on the horizon. By 2026, vulnerability management will face its own set of complex, evolving challenges – technical, operational, and ethical.
Here’s what’s coming, and how we plan to stay ahead of it.

Volume Overload
The number of identified software vulnerabilities is expected to grow exponentially. With thousands discovered monthly, organizations will drown in alerts without automation that can filter signal from noise.
The challenge will be triage - deciding what matters most when everything seems critical.

False Positives and Fatigue
More data doesn’t always mean more clarity. Automated scanners, no matter how advanced, still generate false alarms.
By 2026, system vulnerability fatigue will become a real issue, with teams struggling to distinguish true risk from background chatter. The winners will be those who can combine AI precision with human judgment - a balance Tech360 already masters.

Shadow IT and Untracked Assets
In a hybrid world, teams spin up new tools, cloud instances, and endpoints faster than governance can catch up. These unmonitored assets create silent security vulnerabilities that attackers love.
Tracking every component across sprawling environments will demand stronger asset intelligence and continuous mapping -no exceptions.

Fragmented Security Ecosystems
With cloud, IoT, and edge computing expanding, organizations rely on dozens of security tools - none of which like talking to each other.
This fragmentation makes network vulnerabilities harder to detect, as attackers exploit the cracks between systems. The challenge ahead is interoperability -creating unified platforms that share context across tools.

Weaponized AI and Autonomous Exploits
By end of 2026, attackers will use AI to discover and exploit weaknesses faster than humans can patch them.
We’ll see cyber vulnerabilities exploited within hours of disclosure - forcing defenders to deploy automated countermeasures powered by the same intelligence. It’s a race between two algorithms, and one of them doesn’t sleep.

Compliance Pressure and Limited Resources
Organizations will face stricter mandates but smaller teams. Security budgets might grow, but expertise won’t scale as easily.
Balancing compliance, cost, and continuity will test even the most mature vulnerability programs - especially for businesses operating across borders.

Cloud and Container Complexity
Containers, serverless environments, and microservices multiply fast - and so do their weak points.
System vulnerabilities in cloud-native stacks will require entirely new testing models that understand ephemeral workloads and infrastructure-as-code.







The takeaway
The biggest challenge isn’t just managing vulnerabilities – it’s managing change. Technology moves fast; oversight rarely does.
At Tech360, we’re not chasing threats; we’re anticipating them – turning vulnerability management from a burden into a blueprint for resilience.
The Tech360 Difference
Continuous Vigilance
Context-Driven Reporting
Human Expertise Meets Automation
Compliance-Ready Frameworks
End-to-End Support
Our Approach

We map your environment -identifying assets, endpoints, and exposure points.
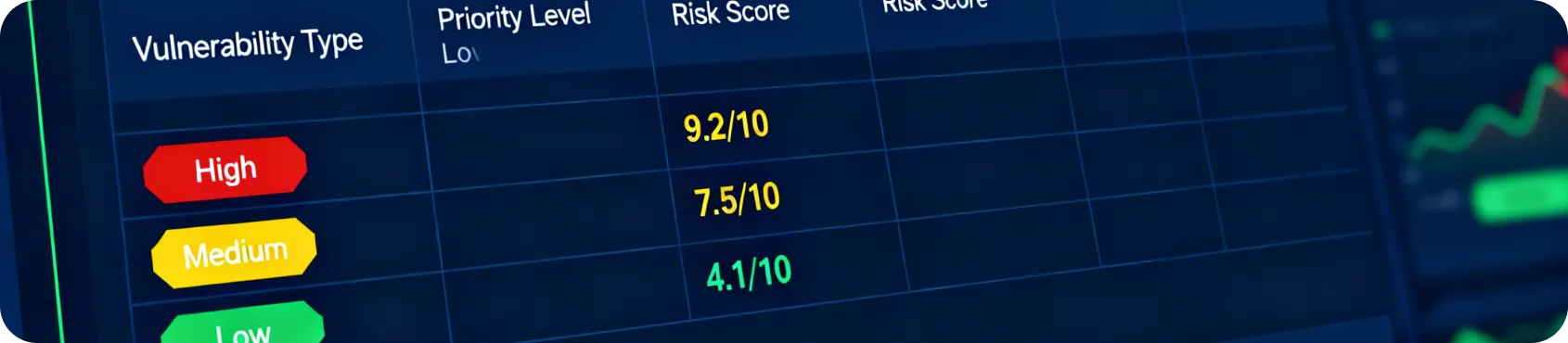
Using advanced tools and expert validation, we identify and prioritize all known and emerging software vulnerabilities.

We collaborate with your teams to close gaps efficiently through guided patching and configuration tuning.

Our team re-tests fixed vulnerabilities to ensure no backdoors remain open.

Through ongoing scans, intelligence updates, and reporting, we maintain an adaptive defense posture that matures with your infrastructure.
FAQs
Frequently Asked Questions
A security vulnerability is a weakness or flaw that can be exploited to compromise systems or data. It can exist in software, hardware, or even configuration. At Tech360, we help identify, prioritize, and remediate these vulnerabilities before they can be weaponized; protecting both your business and your customers.
We use automated scanners, manual validation, and continuous monitoring to uncover software vulnerabilities in applications, operating systems, and third-party components. Our experts cross-reference results with real-world exploit data to ensure findings are accurate and relevant -no false positives, no wasted time.
How Often Should At minimum, every quarter - but ideally, continuously. New cyber vulnerabilities appear daily as software updates roll out and attack tactics evolve. Tech360 provides automated, round-the-clock monitoring that ensures you’re never caught off guard between assessment cycles.
Scanning identifies potential weaknesses; testing exploits them. Vulnerability management focuses on identifying and prioritizing system vulnerabilities, while penetration testing validates how exploitable they truly are. Both complement each other - scanning is prevention, testing is proof.
Our experts perform comprehensive network vulnerability analysis - scanning routers, switches, and endpoints for misconfigurations or outdated protocols. We prioritize findings by impact and urgency, ensuring your network is resilient, compliant, and continuously optimized against evolving threats.
Threat intelligence helps link cyber vulnerabilities to real-world attacks. Tech360 integrates global data feeds to understand which vulnerabilities are being actively exploited. This allows us to prioritize patches and responses based on actual threat context -not just theoretical risk.
Absolutely. Regular assessment and documentation of software vulnerabilities are essential for frameworks like GDPR, HIPAA, and PCI DSS. Tech360 provides reporting that aligns with regulatory standards - ensuring your business stays both secure and compliant.
Because we don’t stop at detection. We deliver clarity, remediation, and measurable improvement. Our team combines automation with human analysis to address network vulnerabilities, software flaws, and compliance gaps. Tech360 turns vulnerability management from a chore into a strategic advantage.

Every Weak Point Is an Opportunity to Strengthen.
Tech360’s vulnerability management services combine intelligence, automation, and experience to detect, prioritize, and remediate weaknesses before they’re exploited.

Success Stories
Success Beyond Code!



“From Sticky Notes to 100% Seamless Operations”
A regional retailer wanted to “go digital” but was drowning in legacy systems and paper-heavy processes. Tech360 stepped in with digital transformation services that modernized their operations end-to-end — cloud migration, workflow automation, and real-time analytics. Within 6 months, they cut manual tasks by 40%, launched an online storefront, and doubled customer engagement. The CEO put it best: “We used to survive on sticky notes and gut instinct. Now we actually know what’s happening, and customers notice.” Transformation doesn’t always start flashy; sometimes it’s just about finally getting the basics right.

“From Prototype Struggles to Market Success”
A fast-growing startup had an idea for a healthcare app but kept stalling after failed MVP attempts. Tech360’s product engineering services guided them from concept to launch: ideation, prototype, testing, and full-scale development. We built a secure, scalable app that integrated seamlessly with medical devices, all while meeting HIPAA standards. The result? A product that hit the market three months early and attracted a major investor round. That’s the power of structured software product engineering: clarity from day one.

“Turning Salesforce into a Sales Engine”
A mid-sized B2B company had Salesforce but treated it like an expensive Rolodex! Sales reps hated it, managers ignored it, and data lived everywhere but there. Tech360 brought in Salesforce development services and a certified team to customize workflows, integrate third-party systems, and build dashboards that actually answered business questions. Within weeks, sales adoption skyrocketed, reporting accuracy improved by 60%, and quarterly revenue jumped. The client admitted, “We finally feel like Salesforce is working for us, and not the other way around.”